AI-Driven Workflows for Accessible Data and Measurable Impact

‘If you want to take advantage of AI you have to do two things:
(1) Do a good job of organising your existing data and make it accessible, and (2) use appropriate AI tools, whether they’re LLMs or other neural networks…’
Larry Ellison, Oracle.
As organisations navigate their data-rich landscape, AI-driven workflows play a pivotal in turning information into a strategic advantage.
Empowering enterprises by seamlessly integrating AI across workflows, making data not just accessible, but actionable. This AI-driven approach enables our clients to harness insights, streamline decision-making, and drive measurable impact.
That’s why at this year’s CDAO Perth, we demonstrated how AI-driven workflows and data security innovations align with this vision — from pioneering generative AI applications to implementing robust security frameworks.
Contents
The Journey So Far: Leveraging AI-Driven Workflows for Secure, Accessible Solutions
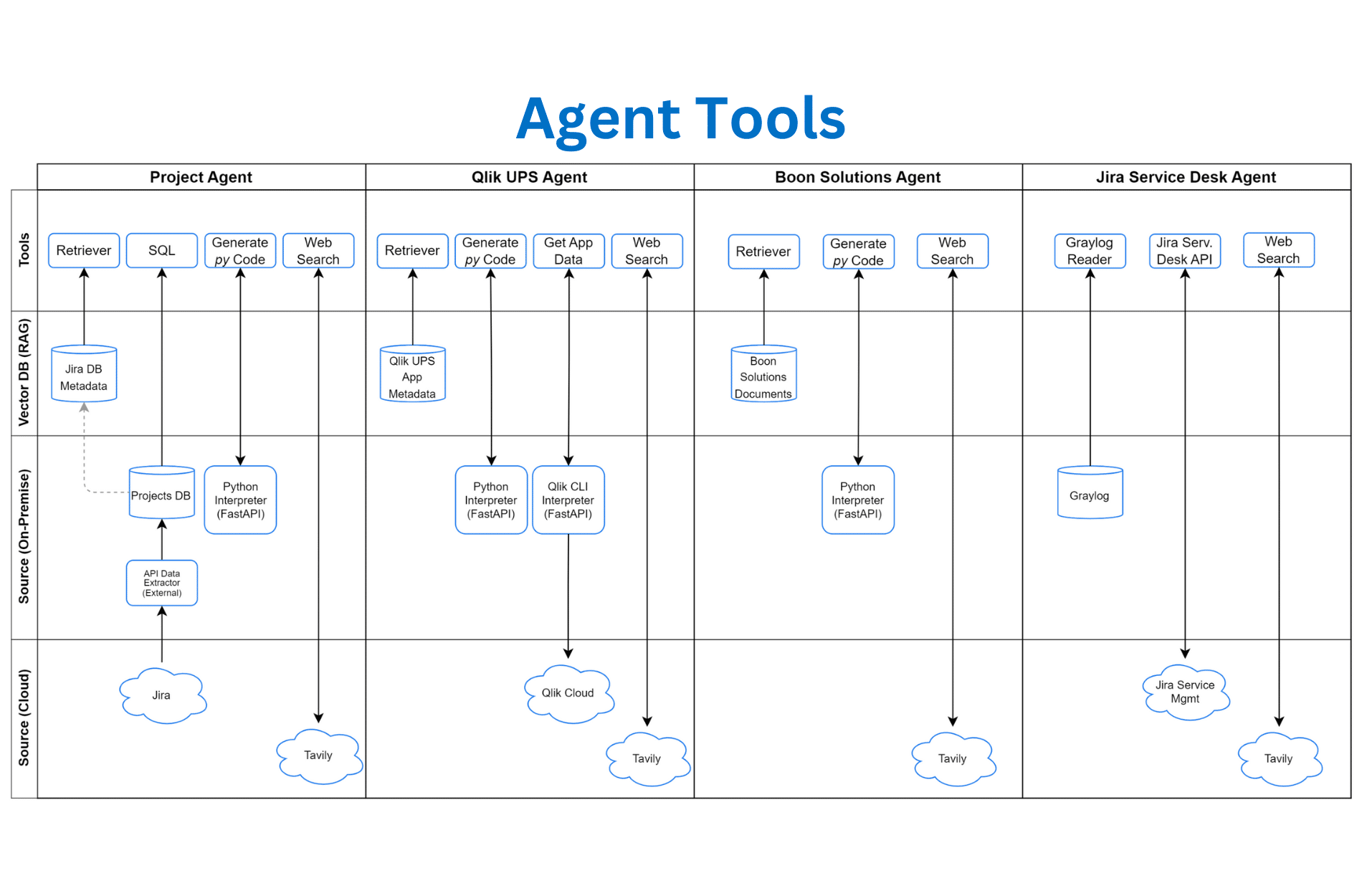
Our journey in AI began in 2023, starting with a subscription of ChatGPT Teams to explore Large Language Models (LLMs). This early phase allowed us to experiment with AI-Augmented Workflows, leading to the launch of our first chatbot at CDAO Perth 2023. Committed to innovation, we have since expanded our R&D in Generative AI, incorporating AI models with the intention to elevate our clients’ data capabilities.
By the end of 2024, we deployed agents capable of routine tasks, set up self-hosted LLMs, and introduced zero-trust networking for data security. This progression laid the groundwork for our 2025 roadmap, where we aim to implement multi-agent AI systems that solve complex challenges collaboratively and enhance productivity.
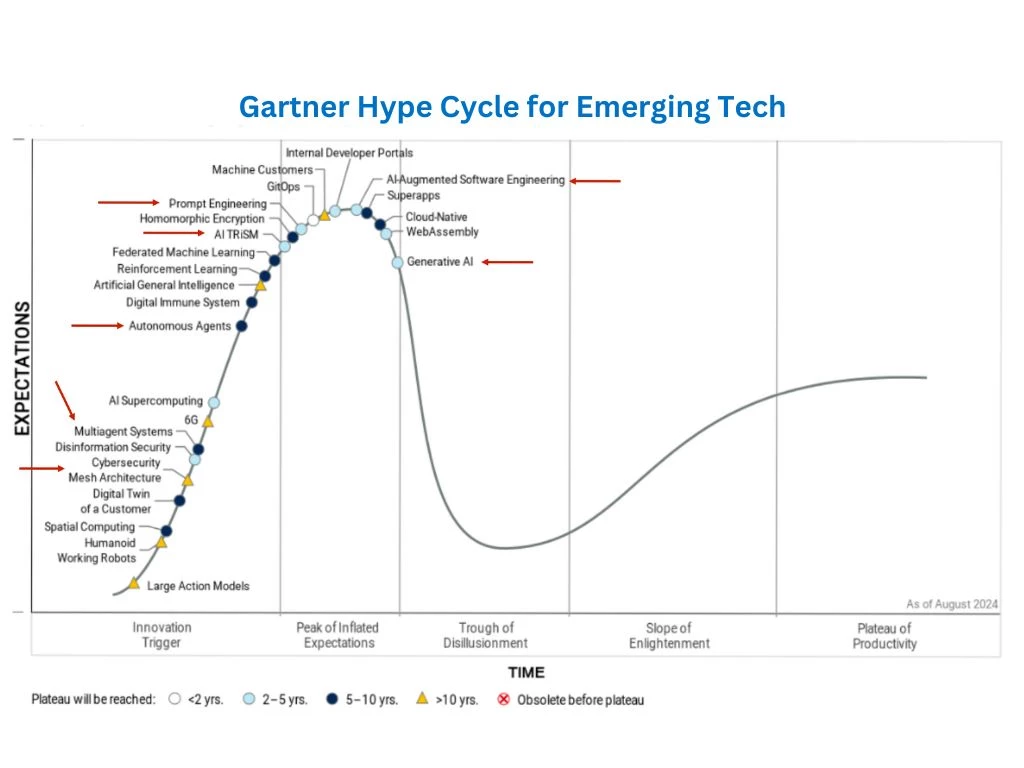
Even as the Gartner Hype Cycle places us in the era of Generative AI and beyond, we are actively exploring advanced technologies that sit on the upward curve; multi-agent systems, mesh architecture, and autonomous agents to redefine AI’s potential. Our development work in prompt engineering and AI TRiSM (Trust, Risk, and Security Management) lays the foundation for secure and ethical solutions. By integrating Generative AI with AI-Augmented software engineering, we are investigating transformative solutions that empower organisations to achieve improved levels of efficiency, scalability, and intelligence.
Security and Data Protection: A Zero-Trust Approach
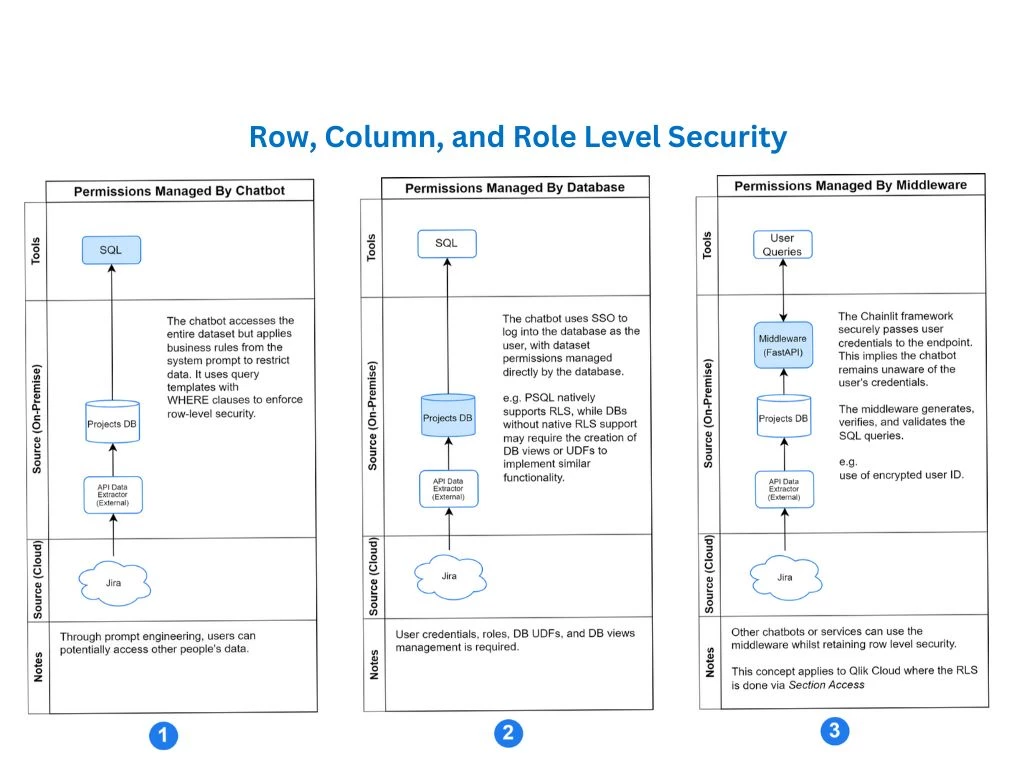
Security is a cornerstone of our operations. Boon Solutions employs a zero-trust framework that includes endpoint protection, secure code execution, access control, data masking, and data replication. As part of our development process we plan management of permissions through a chatbot’s prompt, a database, or a middleware. Each offers different technical approaches with specific advantages and limitations:
Prompt-based permission management. Embedding user identity and business rules directly into a chatbot’s system prompt involves defining user roles, permissions, and business logic in plain language within the chatbot’s initial instructions. The chatbot uses these embedded rules to act as a proxy for database access, interpreting user queries and providing responses based on the defined parameters. This method is straightforward to implement, requiring only the description of business rules and user identities in natural language, making it a quick and low-effort solution for planning, implementation, and execution. However, can present significant security challenges, as the bot may be manipulated through prompt injection or cleverly crafted queries to reveal unauthorised data. To mitigate these risks, combining this approach with contextual analysis, regular prompt reviews, and API-driven access controls is recommended.
Database-layer permissions leverage the database’s native capabilities to manage users, roles, and access controls, with the database administrator defining permission policies for each user or user group. This approach is highly secure since users interact with the database using their own credentials rather than relying on the chatbot as a proxy. While straightforward to implement for simple access policies, it can become increasingly complex and less scalable as the number of users and permission types expands, particularly in high-demand systems where managing diverse access requirements can create significant administrative overhead.
Middleware-based permission management utilises frameworks like FastAPI, and acts as an intermediary layer where permissions are managed via APIs. This allows for more dynamic and flexible access control, such as real-time updates or integration with external systems for role-based (RBAC) or attribute-based (ABAC) access models. The main advantage is scalability and adaptability, especially in multi-layered systems. However, it introduces additional complexity, as the middleware must be securely maintained, and there is an added dependency on API performance.
Each approach has its place, and the choice depends on the specific requirements for flexibility, scalability, and security in the system design.
Planning for the Future: Deciding AI-Driven Workflow that Transform Business Outcomes
In planning for a data-driven future, choosing the right toolset is key to maximising insights and ensuring data security. When deciding between a plug-and-play solution like Qlik Answers and a custom, organisations should consider both their data complexity and security requirements, alongside their long-term business goals.
Qlik Answers: For organisations needing a secure, efficient way to access and analyse data, Qlik Answers provides a robust, plug-and-play solution. With streamlined setup and integration within Qlik’s existing infrastructure, Qlik Answers offers reliable, immediate insights with built-in data protection standards. This solution is ideal for teams looking to quickly deploy a secure, responsive tool for straightforward analytics needs, especially if they prioritise ease of use and minimal customisation.
Custom, Bespoke Solution: For businesses with more advanced data and security requirements, a custom AI Solution allows for enhanced flexibility and deeper control over data handling. These bespoke solutions can be tailored to integrate complex data sources, implement advanced security protocols, and incorporate custom access controls, all while scaling to meet evolving needs. Custom solutions are ideal for organisations with sensitive or diverse data types, requiring stringent security measures and specialised workflows. They provide a future-proof foundation that can adapt to expanding data requirements and increasing security expectations over time.
By planning with both data and security in mind, companies can leverage Qlik Answers for a quick, secure start, while custom solutions offer the depth, adaptability, and security enhancements needed for complex, long-term data strategies.
Ready to put AI in action to elevate your data strategy?
Connect with us to explore how AI can empower your organisation.